Building a VPC Interface Endpoint and connecting to SQS over PrivateLink!
Journey: 📊 Community Builder 📊
Subject matter: Building on AWS
Task: Building a VPC Interface Endpoint and connecting to SQS over PrivateLink!
This project practices Automation.
Using the 6 Pillars of the AWS Well-Architected Framework, Cost Optimisation, Operational Excellence, Security, Performance Efficiency, and Reliability will be achieved in this build.
This week, I built a VPC Interface Endpoint and connected it to SQS over PrivateLink.
For this project, I used Terraform to automate the solution.
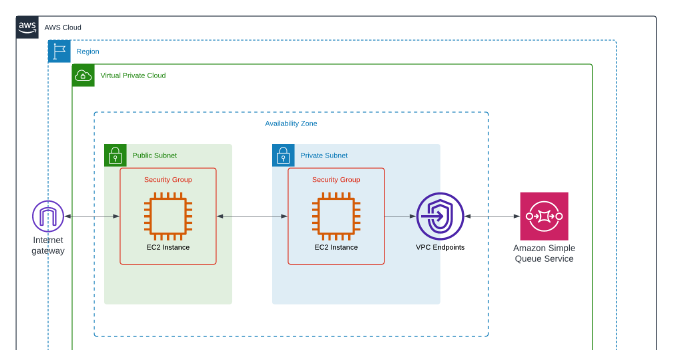
A VPC endpoint enables customers to privately connect to supported AWS services and VPC endpoint services powered by AWS PrivateLink. Amazon VPC instances do not require public IP addresses to communicate with the resources of the service. Traffic does not leave the AWS network.
This is where the cost optimisation comes in! If you were using NAT gateways instead of VPC interface endpoints, your costs would be much higher.

Resource credit: This IaC architecture was created using some guidance from Chinmay Tonape on Dev.to Here.
What did I use to build this environment?
- Visual Studio Code platform
- Terraform
- AWS CLI
- AWS Management Console
What is built?
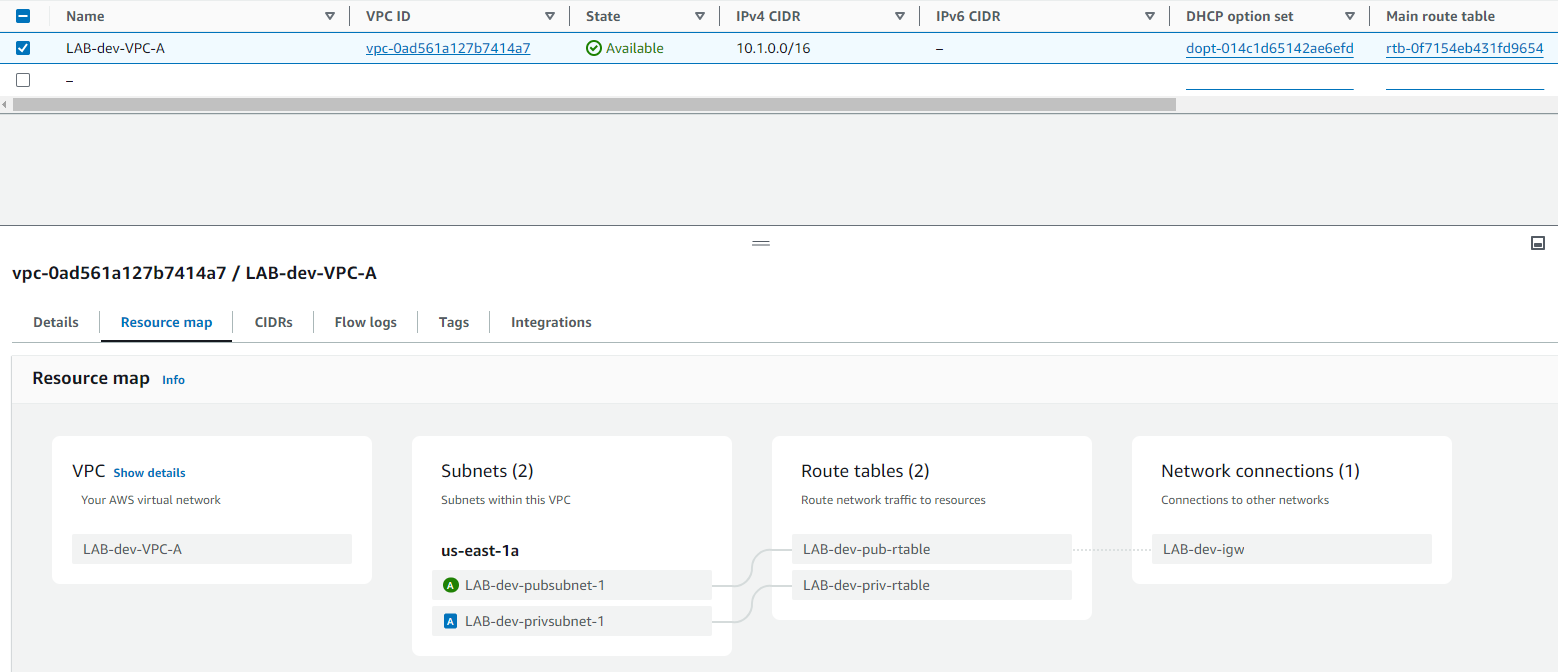
- A single VPC
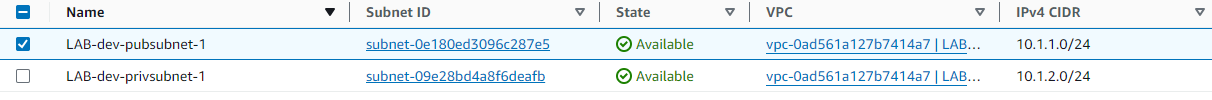
- Public and Private Subnets
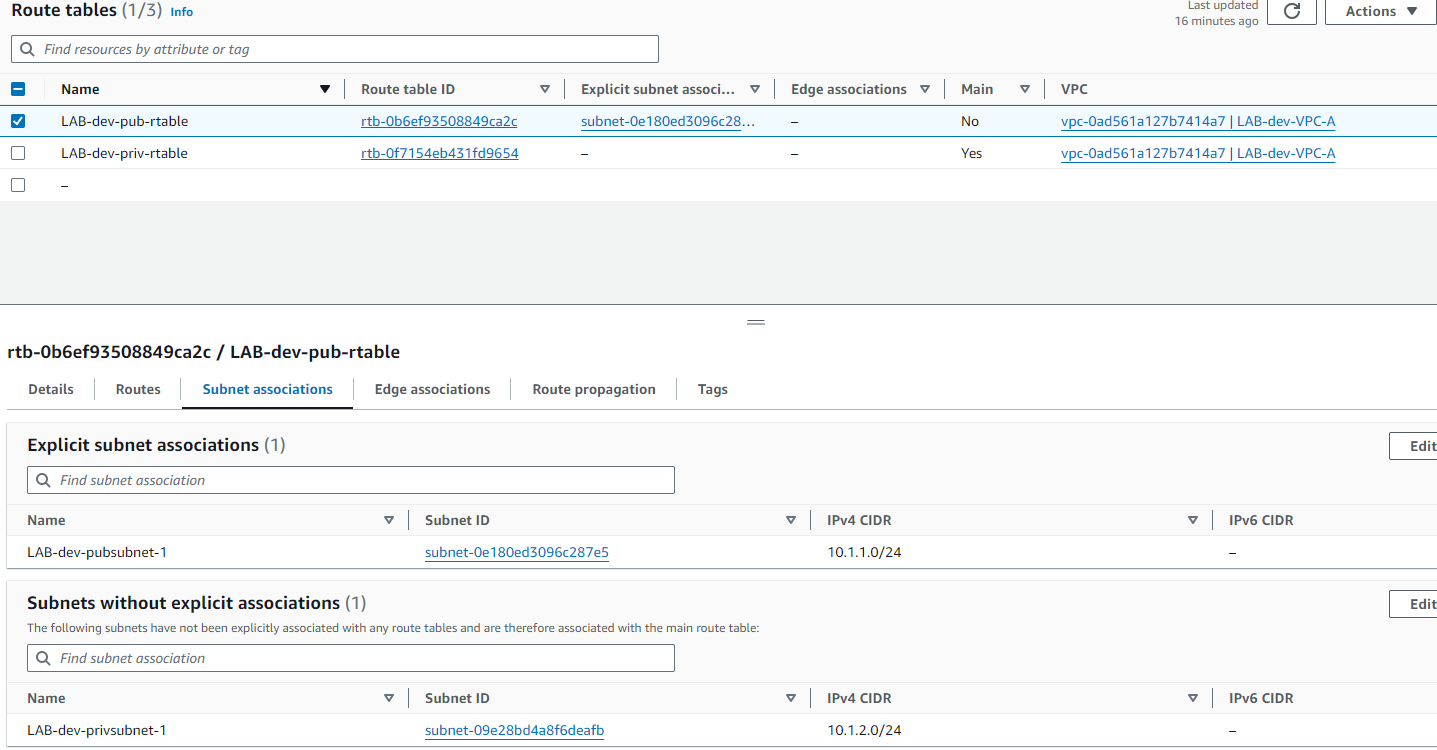
- Custom Route Tables
- Internet Gateway
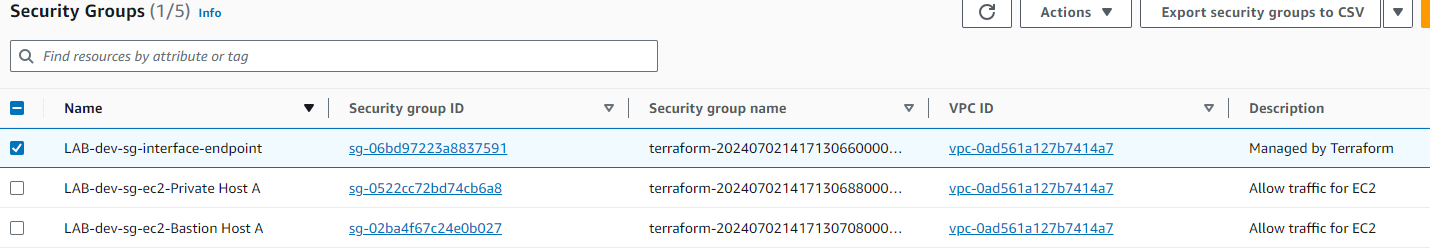
- NACLs and Security Groups
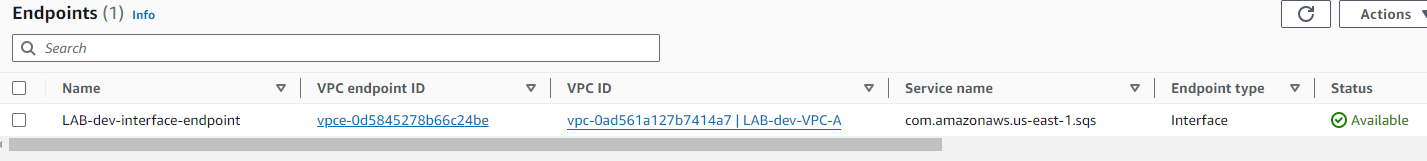
- An Interface Endpoint
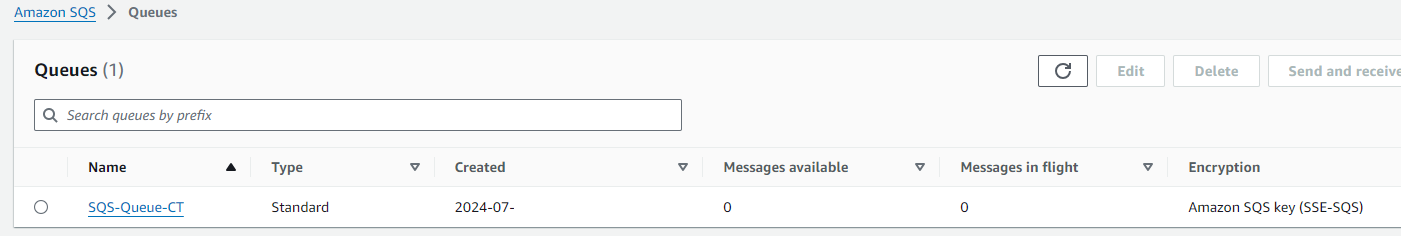
- An SQS Queue
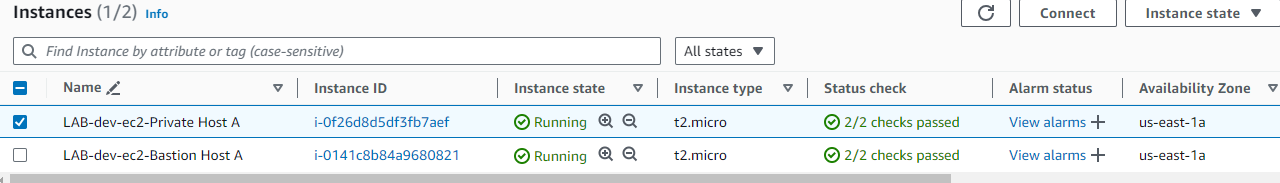
- Public-facing Bastion host
- Private EC2 host
More information on VPC endpoints can be found here: https://docs.aws.amazon.com/whitepapers/latest/aws-privatelink/what-are-vpc-endpoints.html
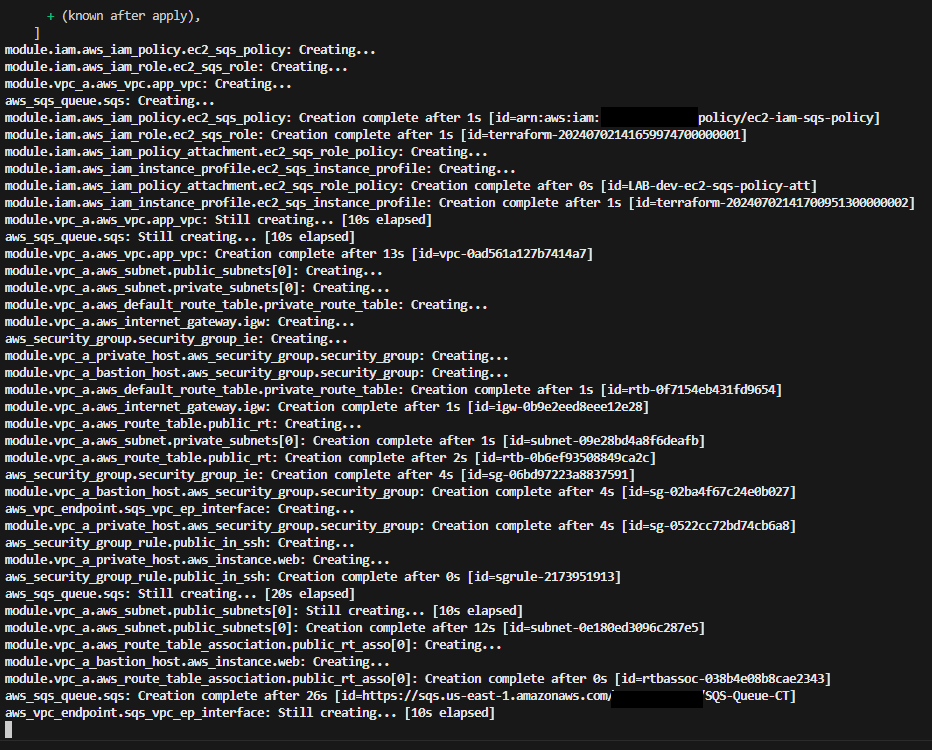
In this task, I used Terraform to build out the environment using some existing key pairs in my designated region.
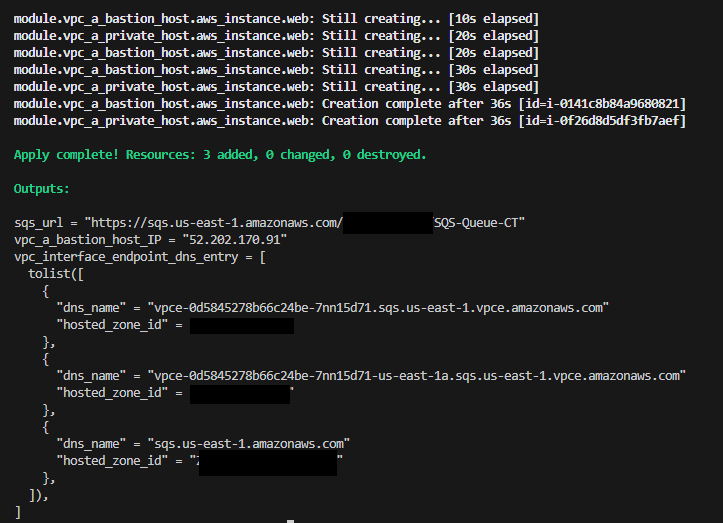
Once Terraform had completed and provided an output, I logged into the AWS Management Console to check everything was correctly applied.
I created a Bastion host in a public subnet and then created an EC2 instance in a private subnet, amending the security group to permit the Bastion host to connect to the private instance.
The SQS queue was created and the VPC Interface endpoint was configured to permit a secure channel to SQS via the private AWS network.
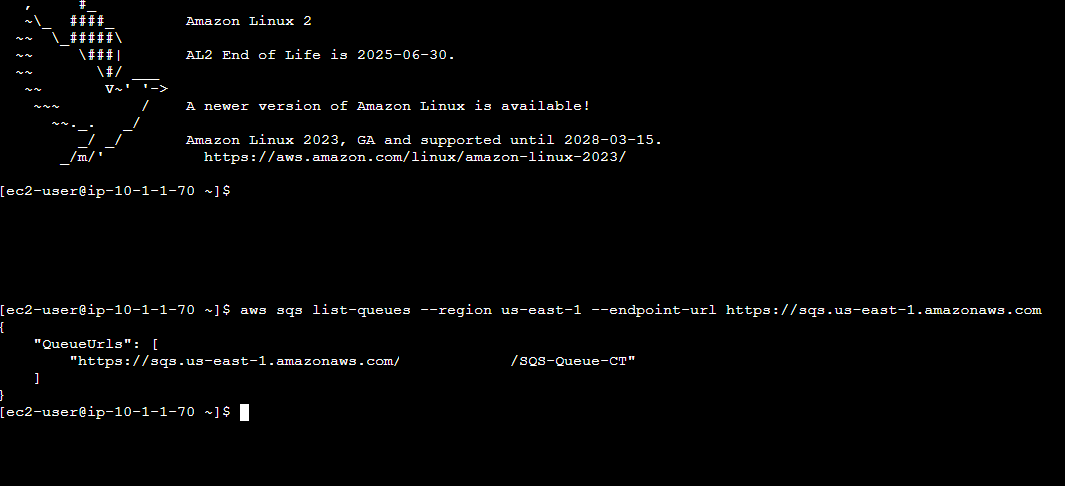
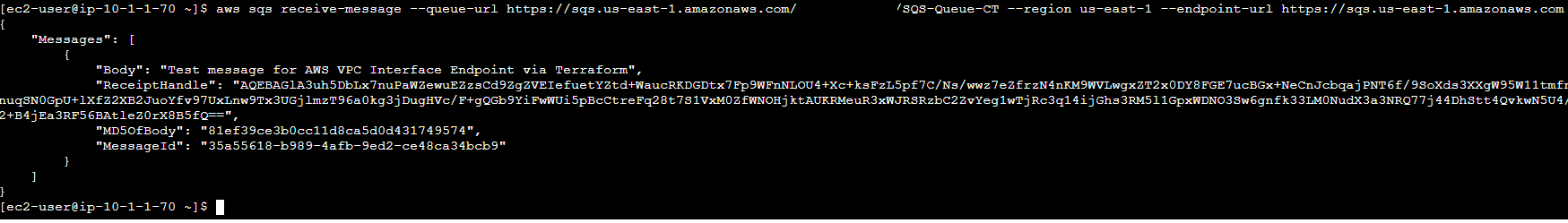
I then configured my Bastion host and ran some SQS queue check commands to see what queues I had available to me before sending a message to SQS from the Bastion host via the private EC2 instance.
After switching to view my SQS queue in the Management Console and polling for messages, I observed it successfully populating the message.
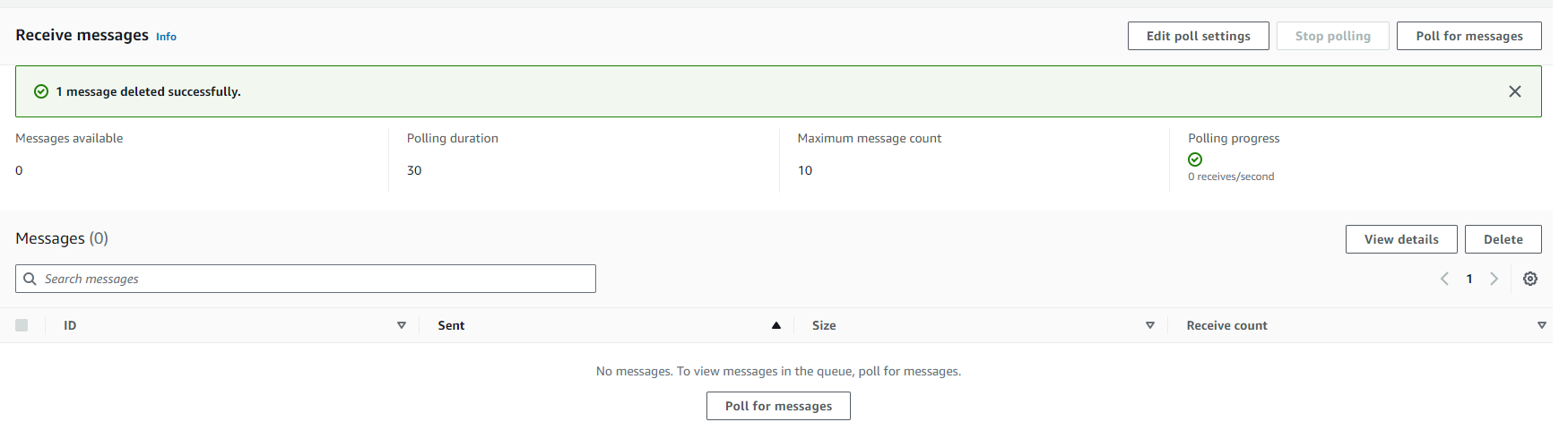
I returned to my Bastion host and requested to receive the same message confirming I could both push and pull data before then deleting the polled message in the console.
As always, running the cleanup is important to prevent unwanted bills so I used Terraform again to destroy the environment!
Some of the highlights…
Terraform start:
Terraform build complete:
VPC:
Subnets:
Route tables:
Interface endpoint:
Security Groups:
SQS Queue:
Instances:
Bastion host SQS Queue list:
Receive message:
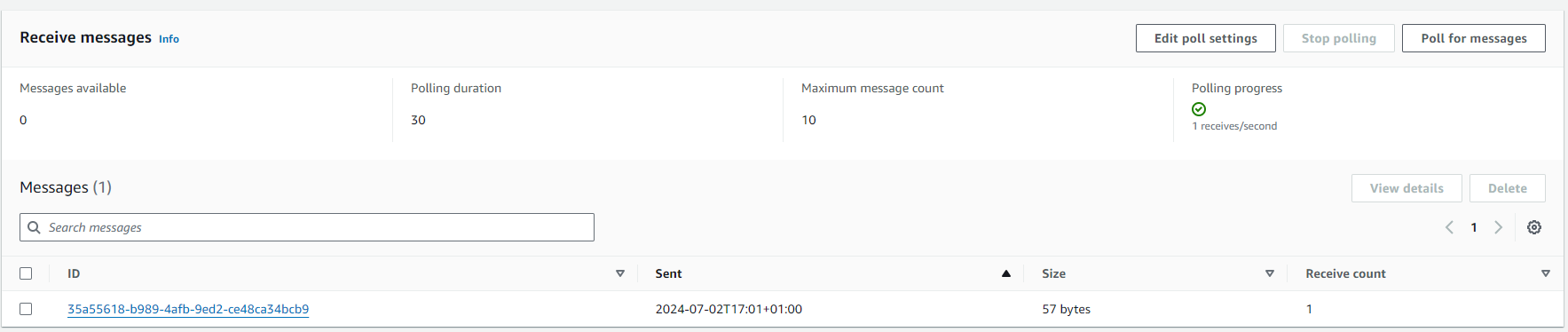
Polling for messages:
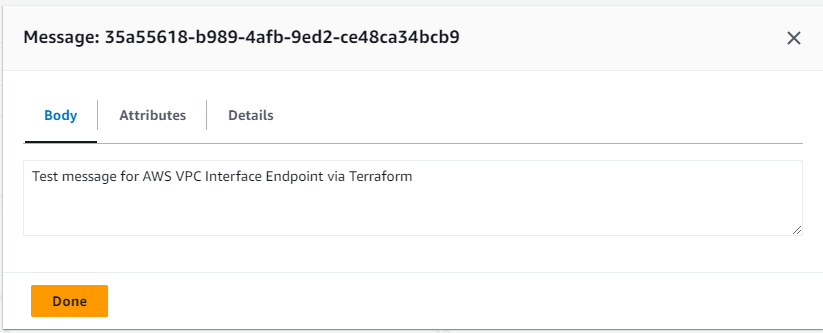
Receive message on Bastion host:
Delete message at SQS:
Terraform destroy:
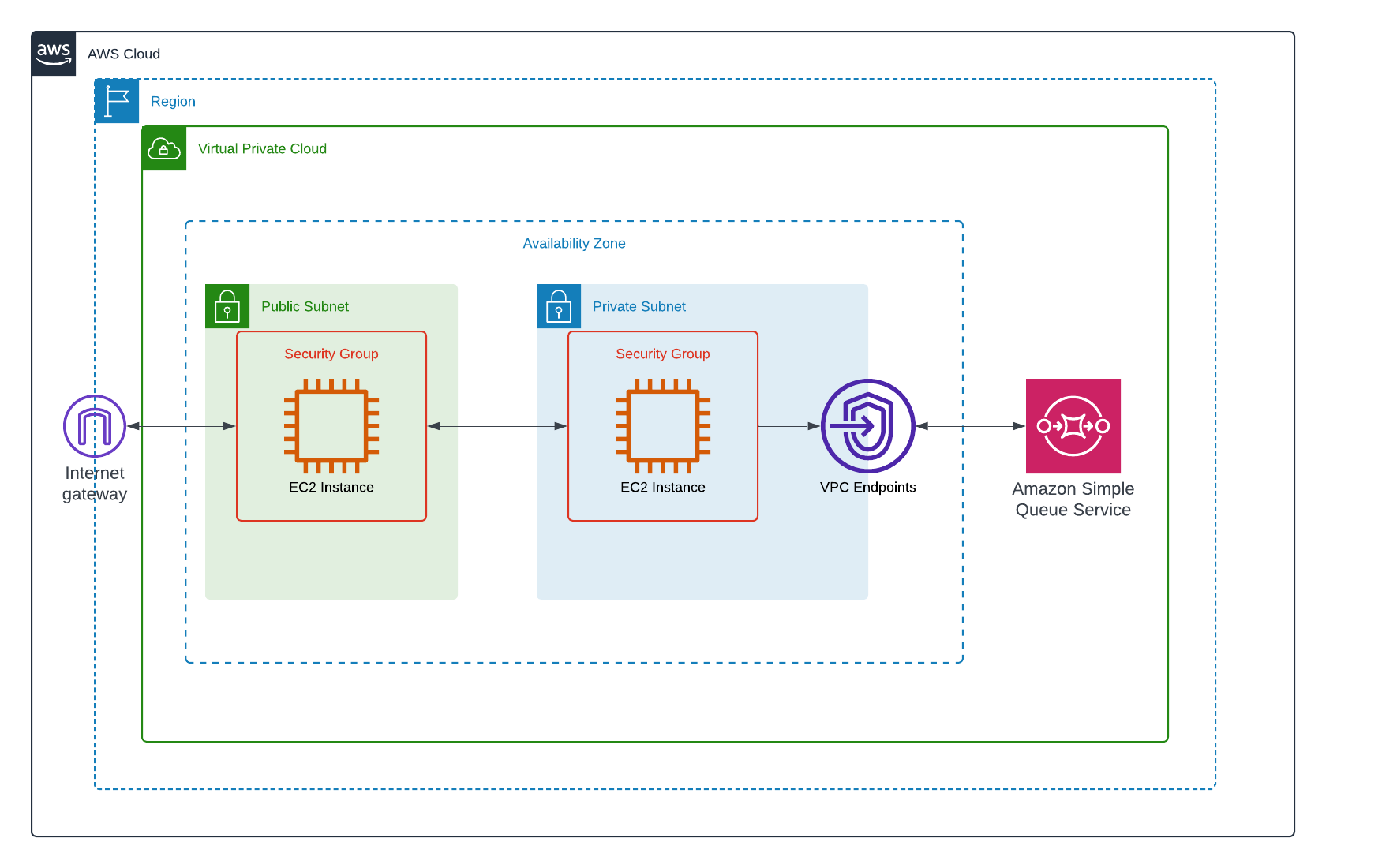
My interpretation of the architecture:
I hope you have enjoyed the article!