Building and configuring EC2 with Terraform and Ansible!
Journey: 📊 Community Builder 📊
Subject matter: Building on AWS
Task: Building and configuring EC2 with Terraform and Ansible!!
Using the 6 Pillars of the AWS Well-Architected Framework, Security, Performance Efficiency, Reliability, and Sustainability will be achieved in this build.
This week, I configured an Ubuntu EC2 instance using Ansible!

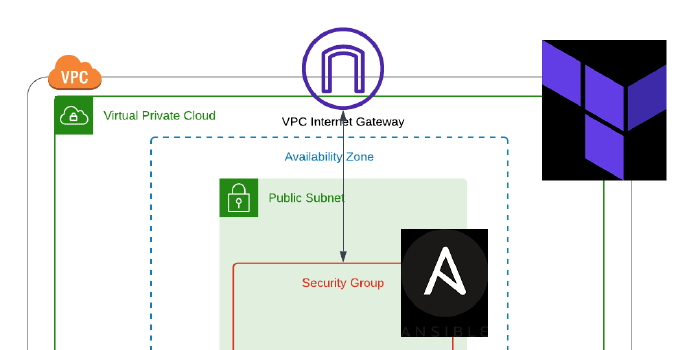
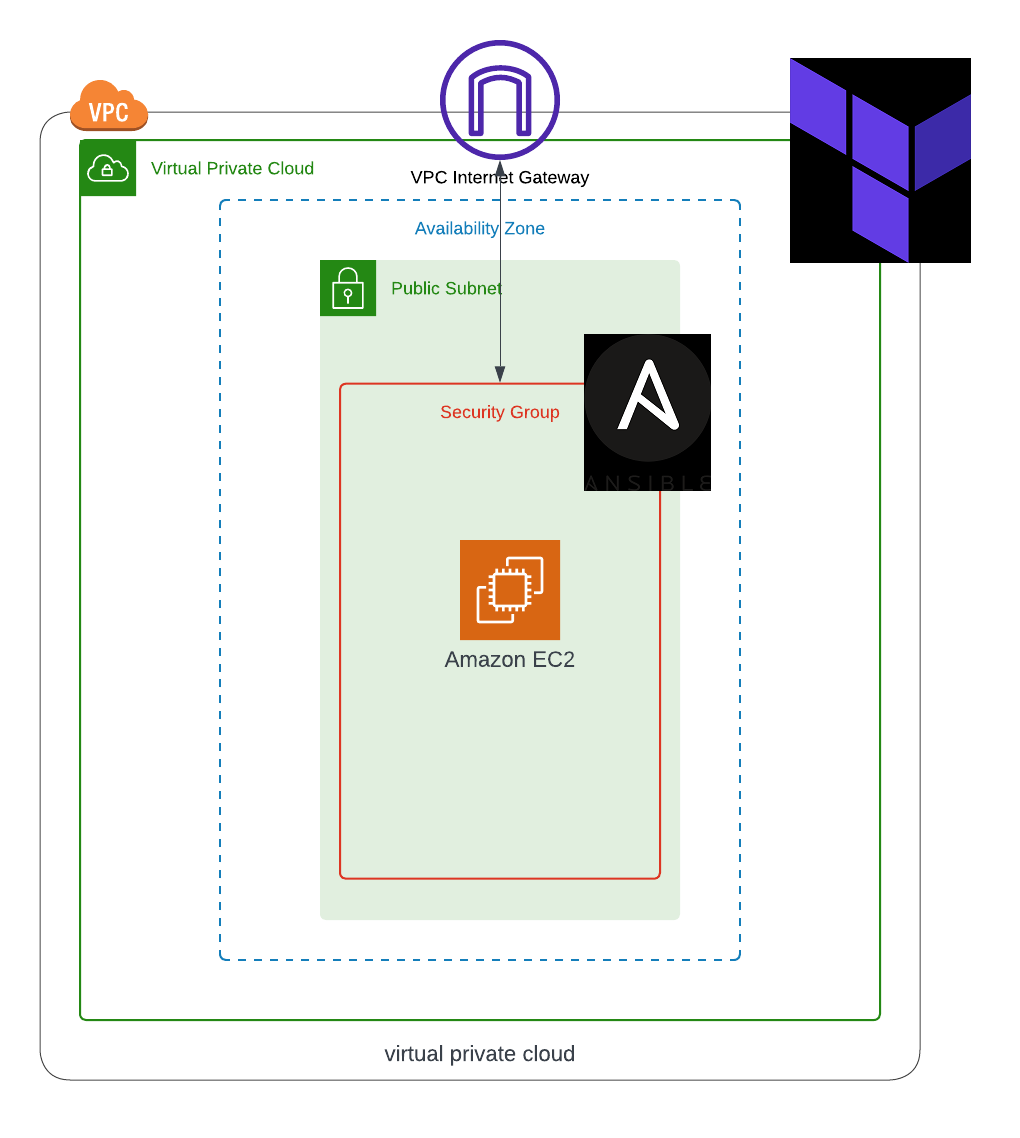
In this scenario, I will be provisioning a new VPC to host an EC2 instance using Terraform, and I will then be switching over to Ansible to configure the instance.
The idea of this environment is to play with Terraform and Ansible, rather than create Highly Available architectures.
Resource credit: This architecture was created using guidance from Alexandr Ivanov Here.
What did I use to build this environment?
- Visual Studio Code platform
- Terraform
- Ansible
- AWS CLI
- AWS Management Console
What is built?
- A single VPC
- A Custom Route Table
- A Security Group
- An Internet Gateway
- One EC2 instance
- A new SSH key
- One website

What I used to help:
https://www.geeksforgeeks.org/install-ansible-in-aws-ec2-server/
https://www.linkedin.com/pulse/use-ansible-aws-host-website-kyle-martinez/
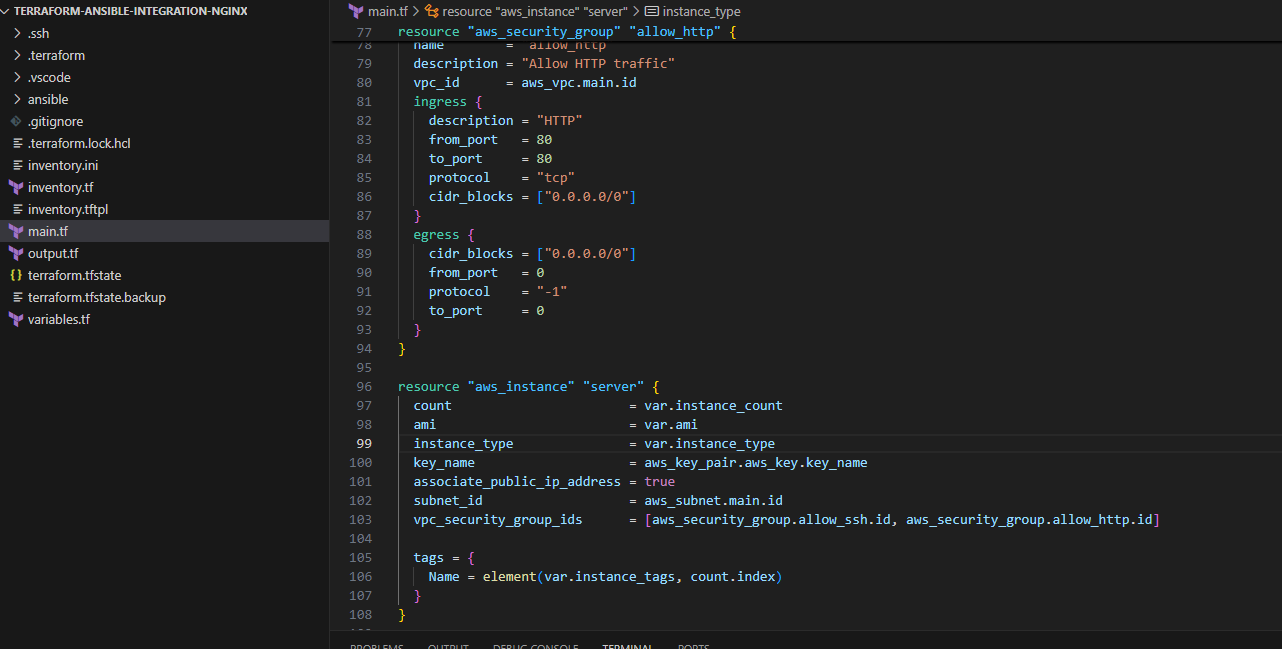
In this task, I started by creating some Terraform files that would later be used to create my base environment, consisting of a VPC, Subnet, Internet Gateway, and EC2 instance.
As always, tag your resources folks!
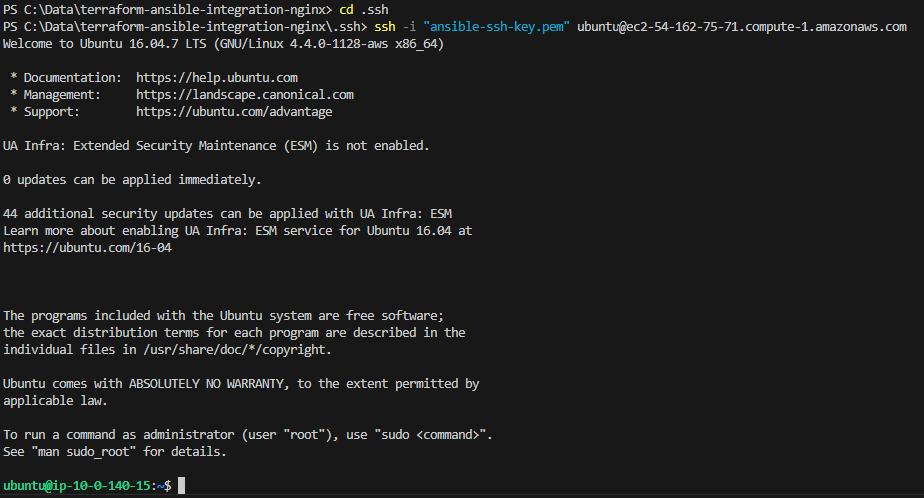
Using the new SSH key, I was able to connect to my Ubuntu EC2 instance. I am using VSCode on Windows so had to SSH directly to my instance before I could pass information via Ansible.
Having never used Ansible before, this was a steep learning event where pretty much everything I had planned didn’t work at first. However, this is where you learn the most, problem solving. It makes you feel so much more confident when you get past the seemingly endless errors on the screen!
I am planning on writing a separate article about one problem that I had to overcome, relating to making my .ssh key read-only to satisfy AWS’s connection standard.
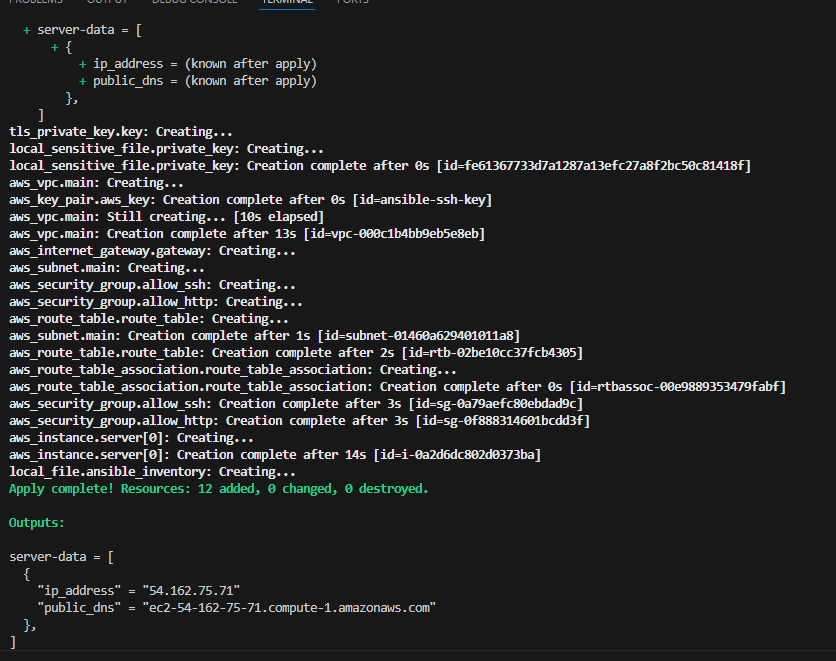
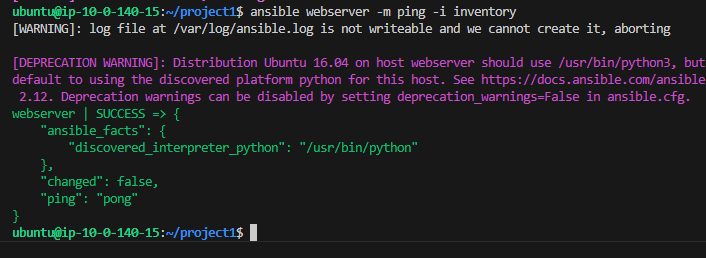
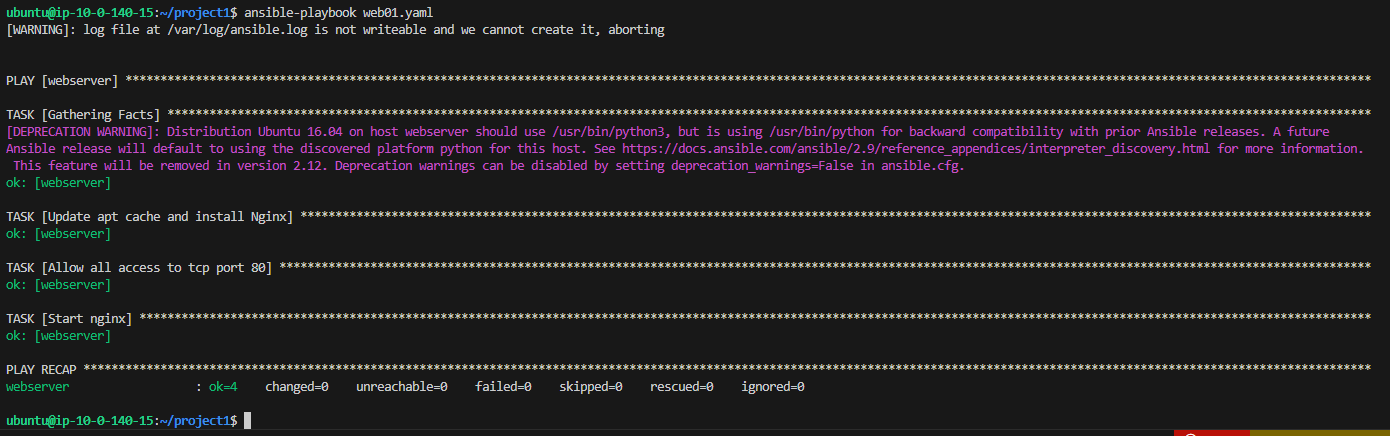
After drafting my Ansible Playbook and configuring the base config, host, and inventory files, I was able to ping my web server. I went ahead and issued a command to run my Ansible Play on the EC2 instance and it completed successfully!
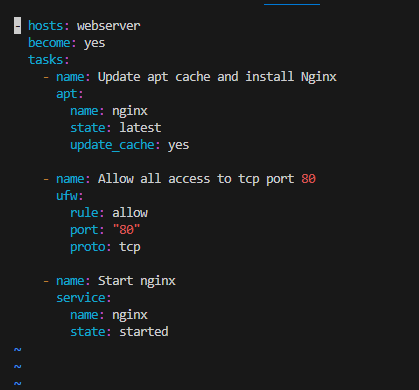
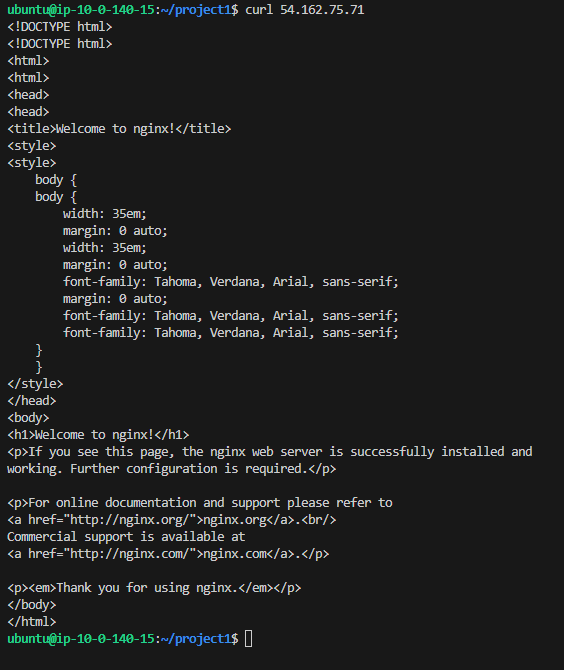
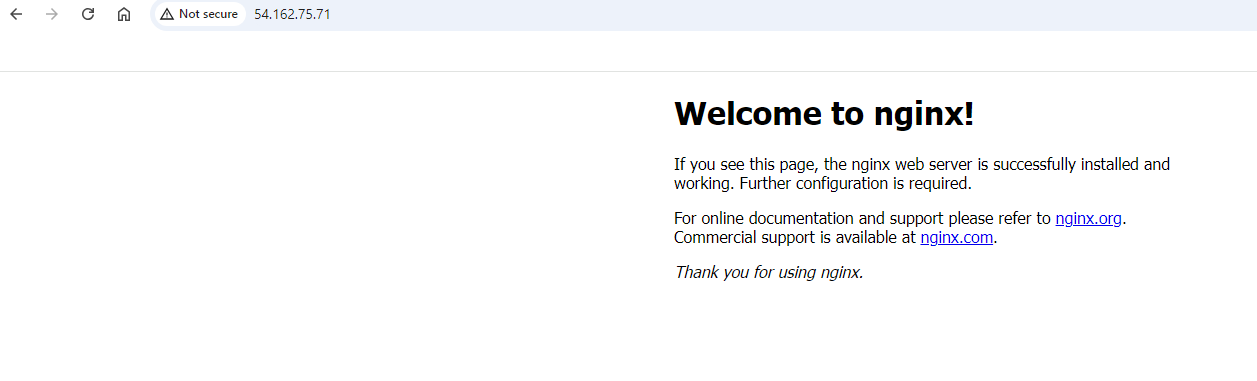
Nginx was installed and my public IPv4 address correctly displayed the default webpage.
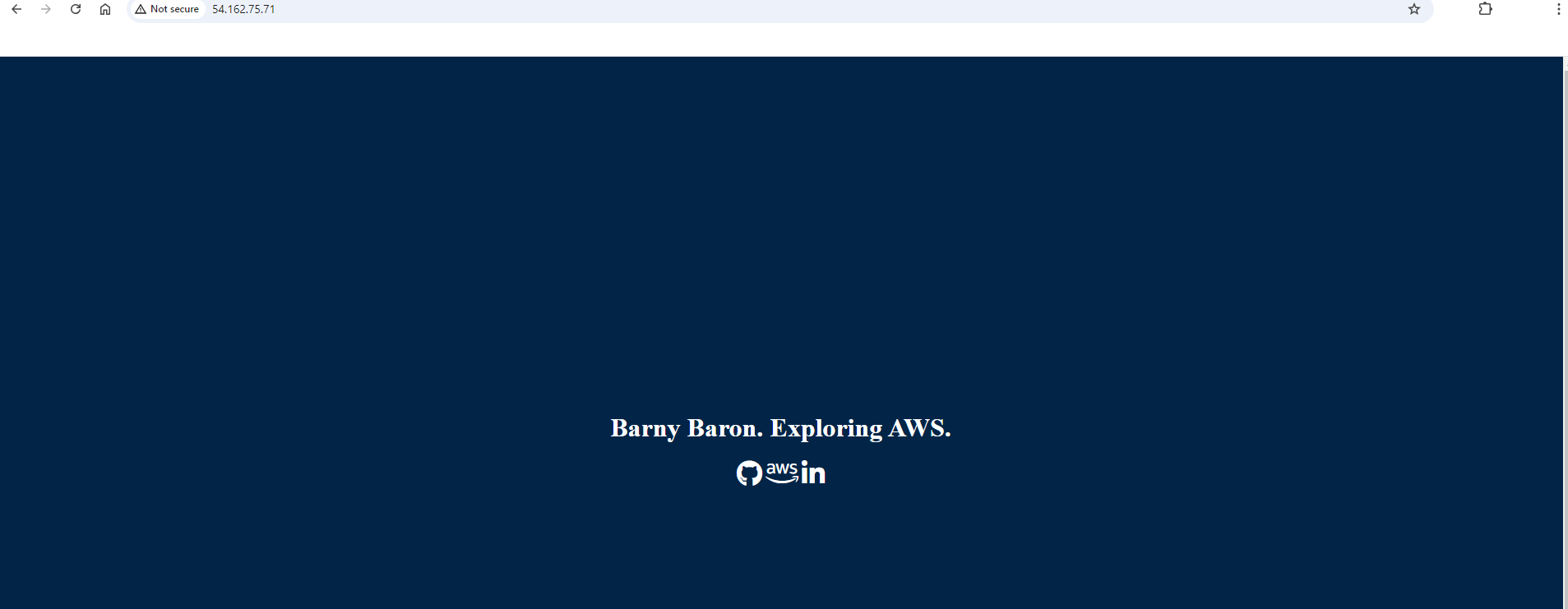
My plan also extended a little further in that I wanted to create a bespoke website front end rather than the standard Nginx page. I created my html, located where it needed to be placed, and then copied my index file over.
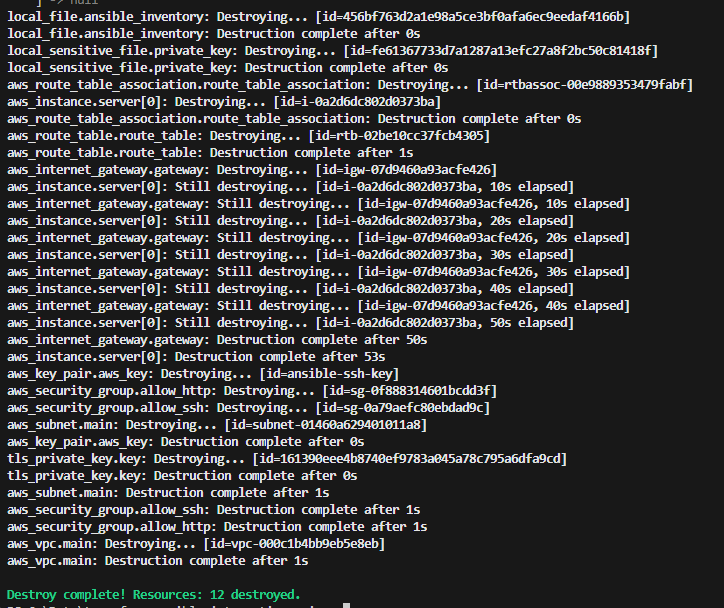
Result: A VPC, running an EC2 instance on Ubuntu, with a web server hosting my bespoke website! All done using Terraform and Ansible!

If I were to expand best practice on this project, I would do the following:
- Have multiple EC2 instances running to ensure High Availability.
- Implement an Application Load Balancer.
- Implement an Auto Scaling Group.
- Utilise an S3 Bucket to host my Terraform state files.
Some of the highlights…
Terraform setup:
Terraform code:
Terraform create:
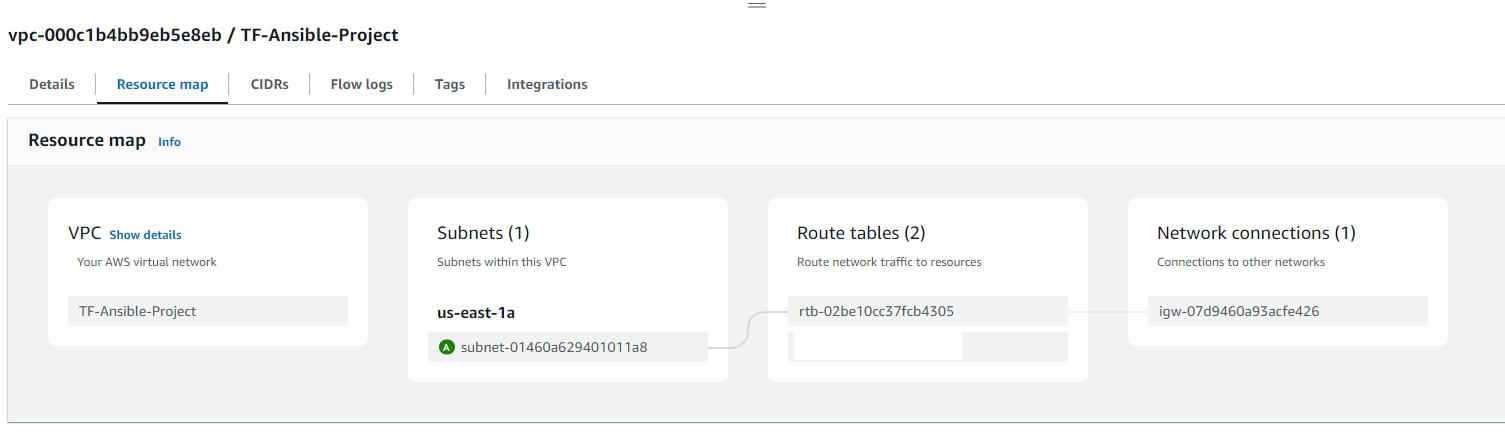
VPC Resource Map:
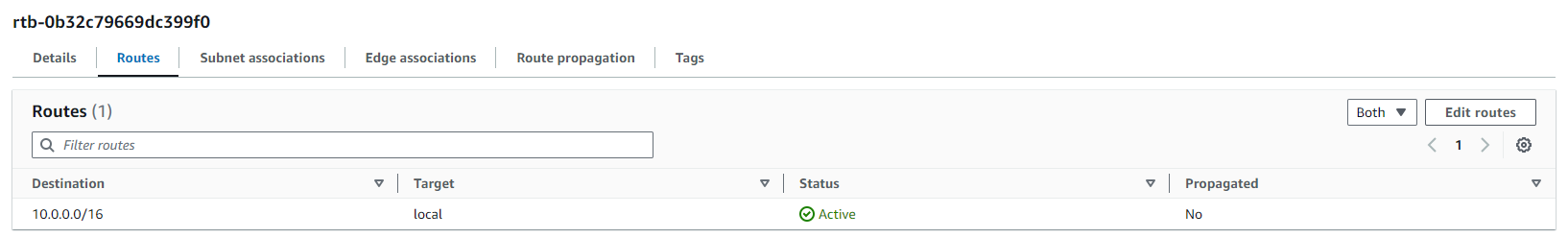
VPC Routes:
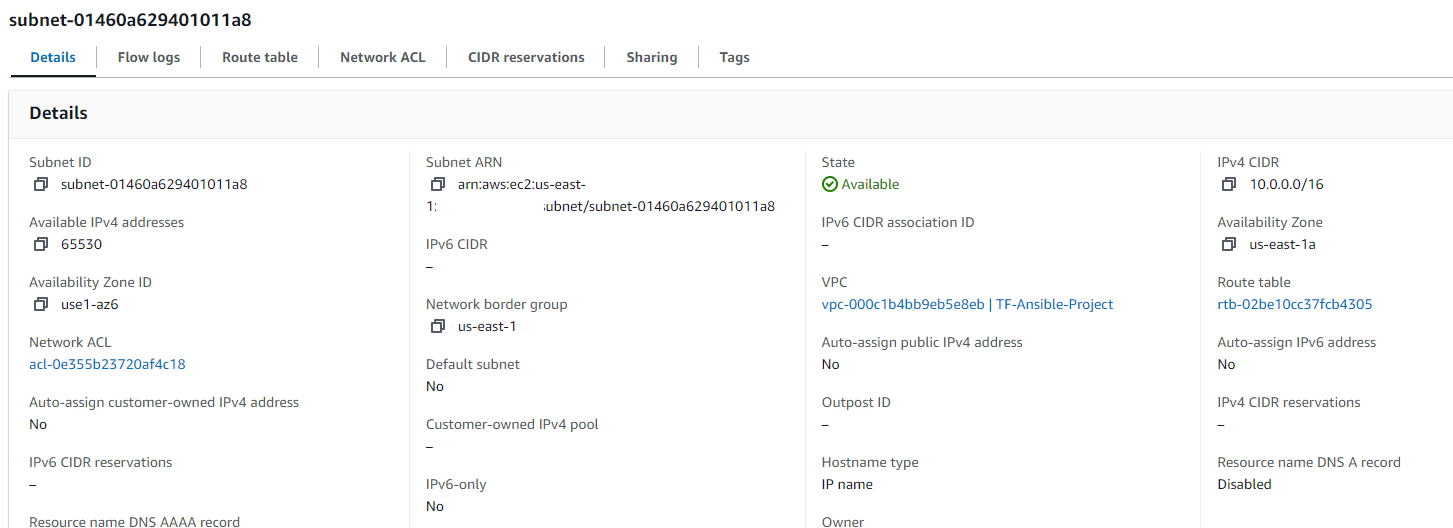
VPC Subnet:
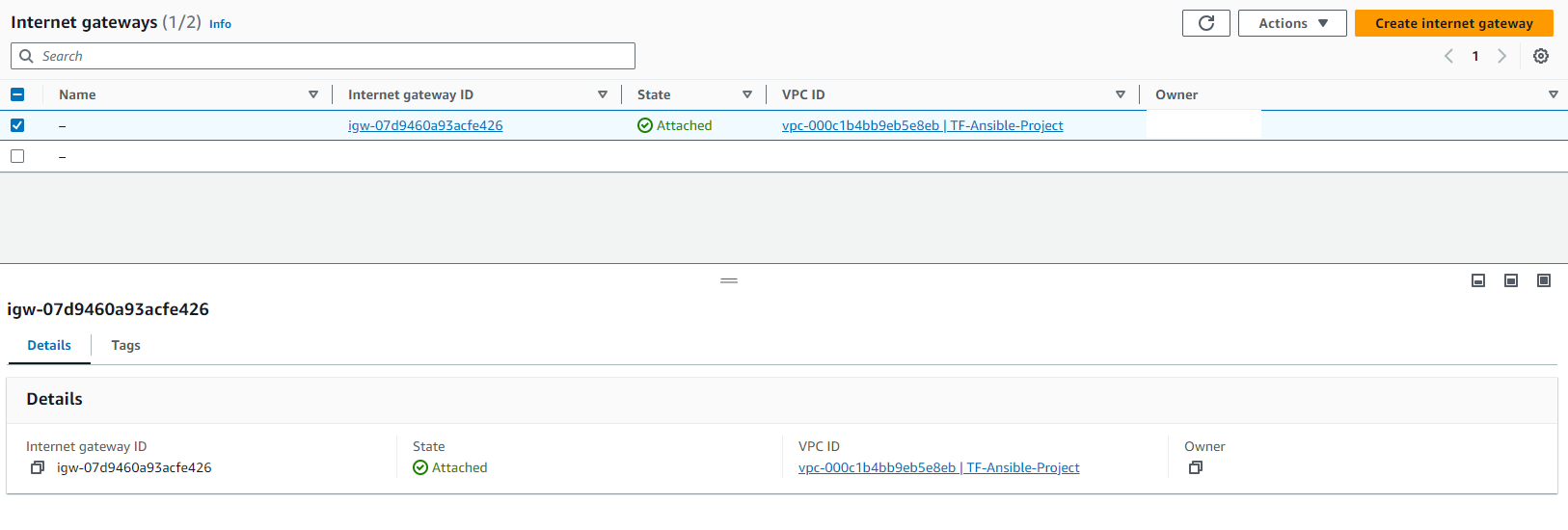
Internet Gateway:
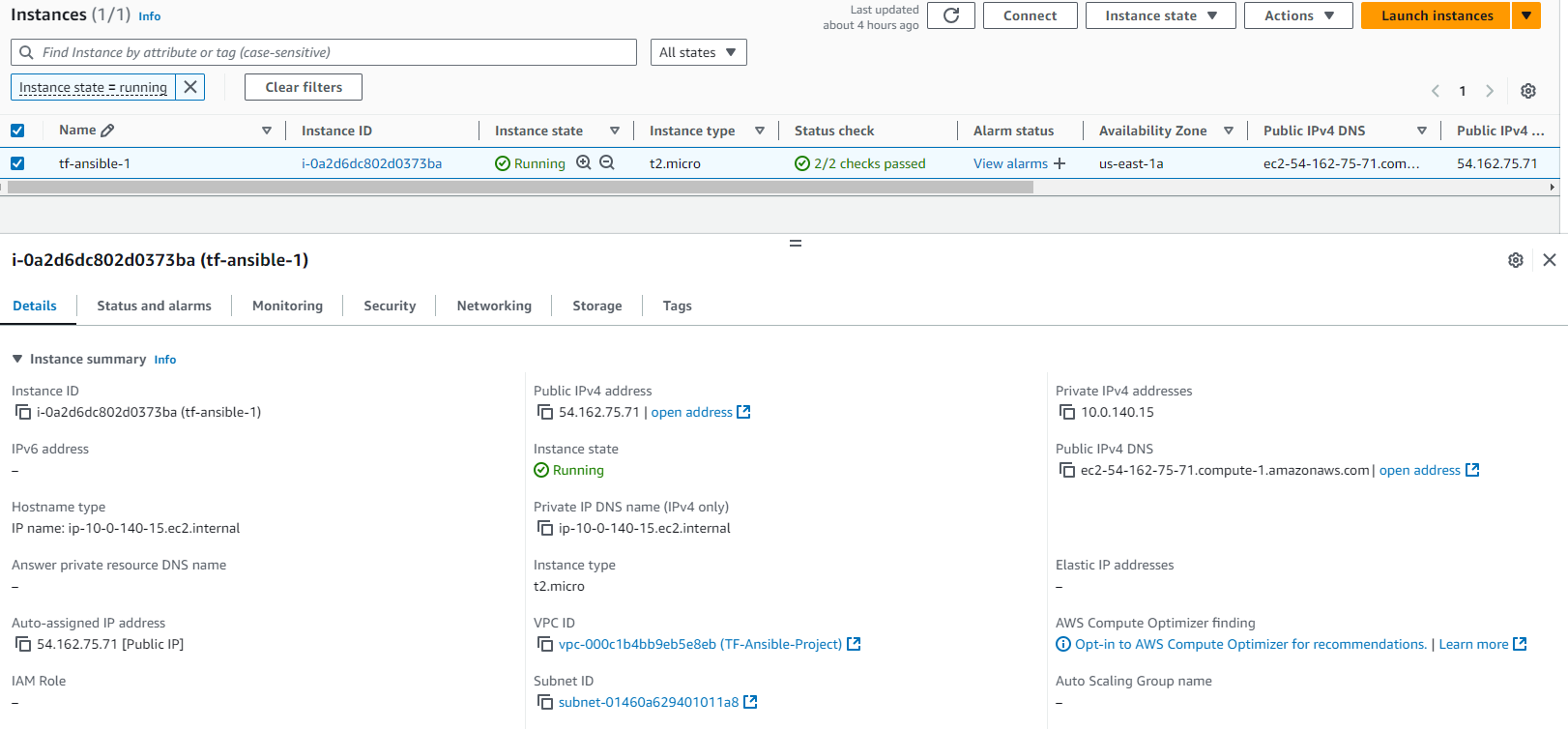
EC2 Instance:
Remote SSH Connection:
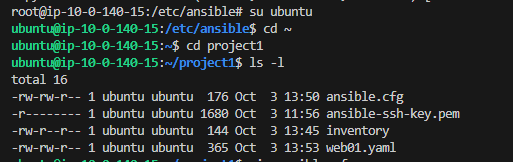
Ansible Project:
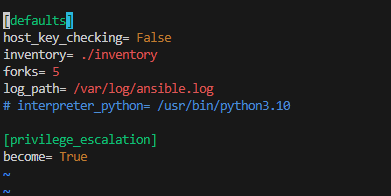
Ansible Inventory:
Ansible Config:
Ansible Playbook:
Ansible Play:
Ansible Website Curl:
Nginx website live:
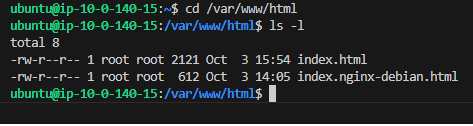
New HTML file:
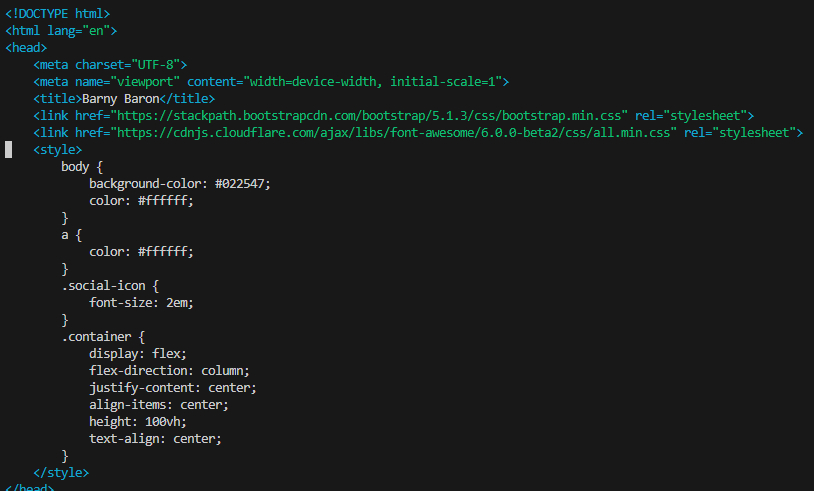
New HTML code:
Resource credit: Here for the cool static HTML base code which I amended to suit.
Bespoke HTML update:
Terraform Destroy:
My interpretation of the architecture:
I hope you have enjoyed the article!