Building a Secure API Gateway using Amazon Cognito!
Journey: 📊 Community Builder 📊
Subject matter: Building on AWS
Task: Building a Secure API Gateway using Amazon Cognito!
Using the 6 Pillars of the AWS Well-Architected Framework, Security and Reliability will be achieved in this build.
This week, I built a Secure API Gateway using Amazon Cognito.
For this project, I used the AWS Management Console to build the environment.

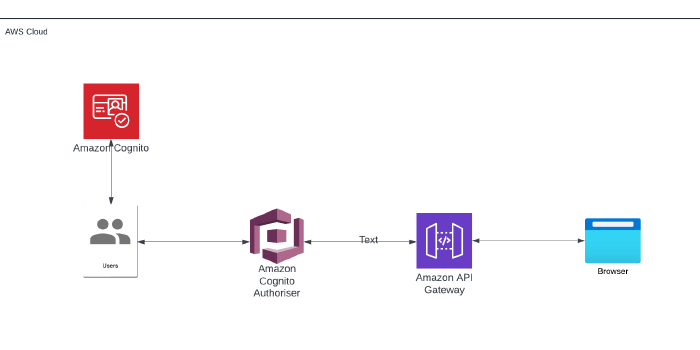
When creating an API, you can use Amazon Cognito - specifically a User Pool - to control who has access to the API in the API Gateway.
To do this, you need to create a Cognito authoriser and then link your API method to the authoriser.
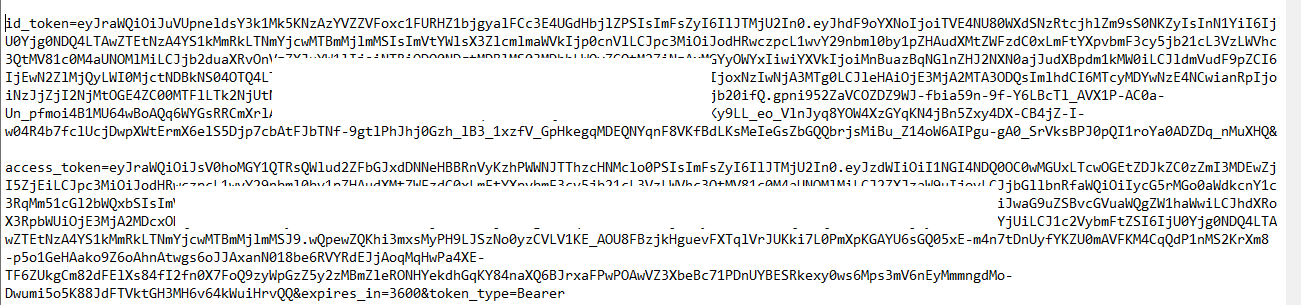
Once an authenticated user logs in, they obtain an ID token and are able to call the API using the token.
For this project, I am using Postman to call my API and will show the various responses you receive with and without an ID/Access token.

Resource credit: This IaC architecture was created using guidance from Mathesh Yogeswaran on Medium Here.
I had some problems with the authentication side of the build, so I reached out to Mathesh. We worked together to troubleshoot the environment and overcome the issue, which was a great collaborative effort. Please be sure to check out his articles.
What did I use to build this environment?
- AWS Management Console
- Postman API Platform
What is built?
- An API Gateway [REST API]
- Cognito User Pool with Cognito Hosted UI
- Cognito Users
- Cognito Authoriser
More information on Cognito Authorisers can be found here: https://docs.aws.amazon.com/apigateway/latest/developerguide/apigateway-integrate-with-cognito.html
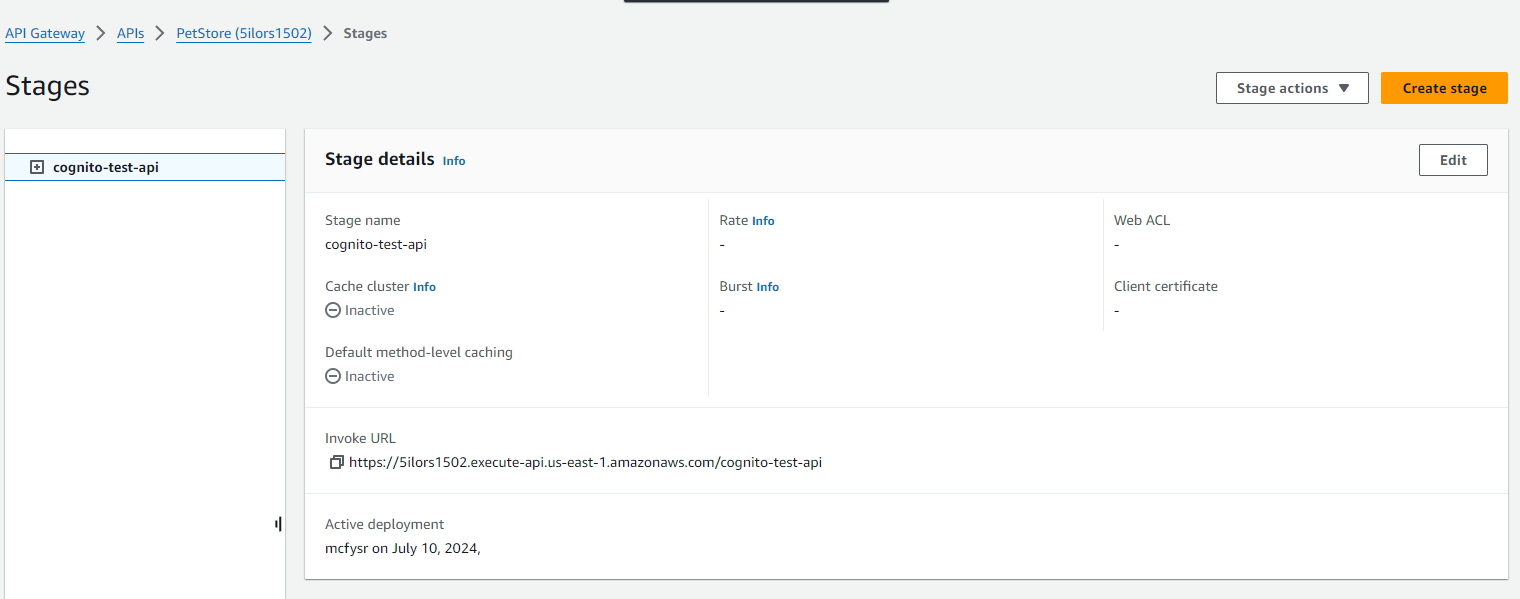
In this task, I created a REST API Gateway with an example API and then deployed it.
After receiving my invoke URL, I was then able to call the publically accessible URL in the Postman API platform successfully.
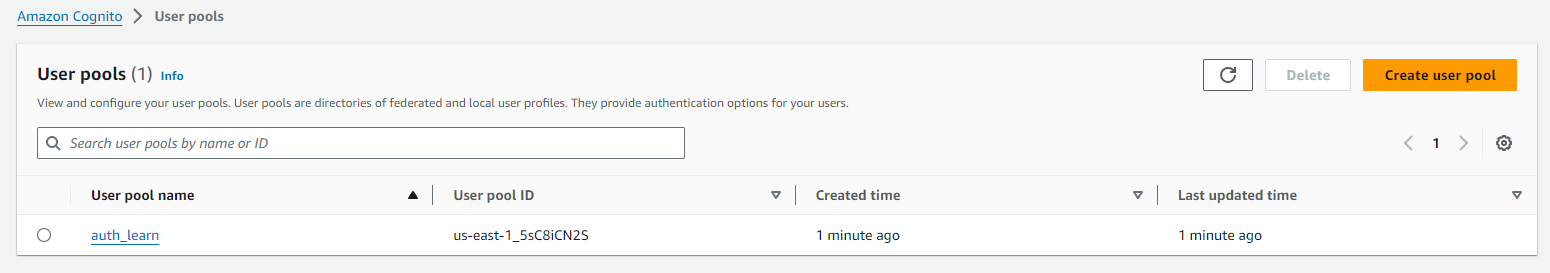
I then created a Cognito User Pool using Email as the authentication provider and with no MFA requirements.
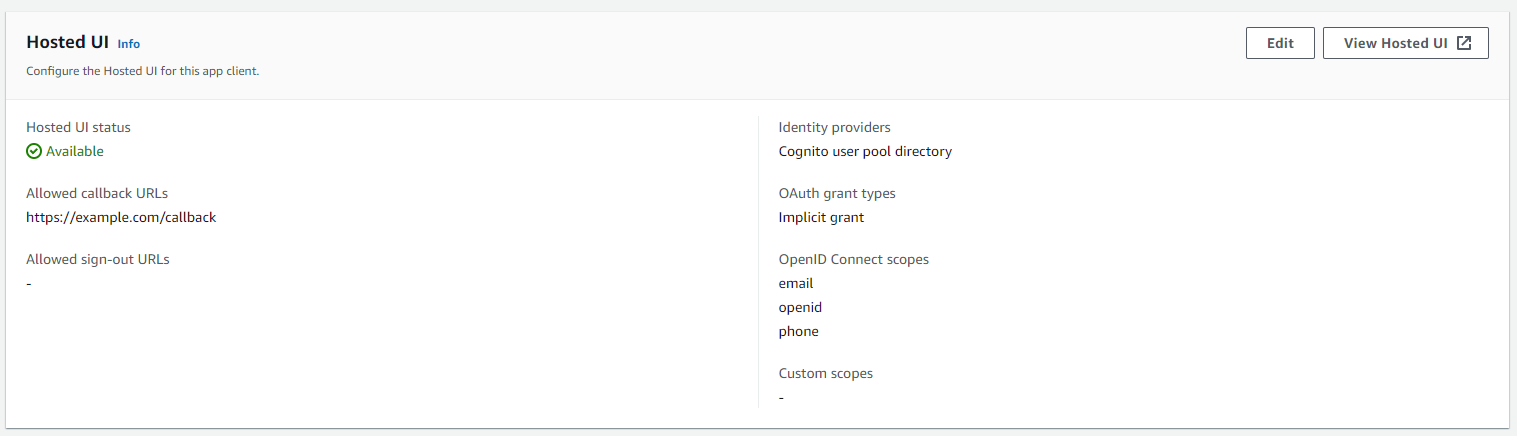
I integrated the User Pool with a Cognito Hosted UI and provided a callback URL.
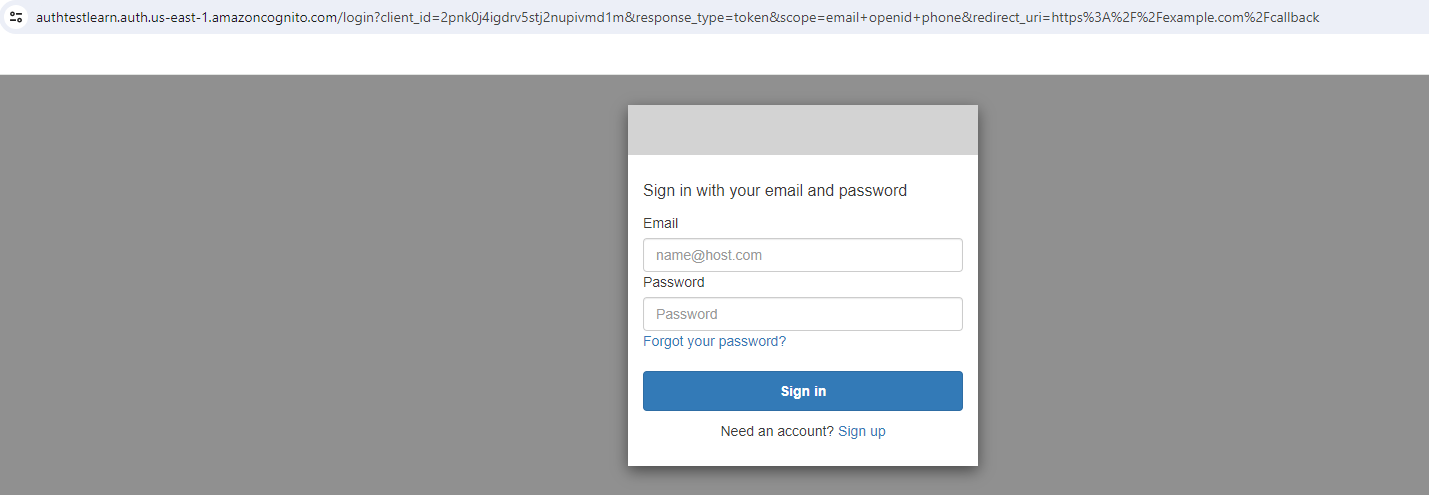
After completing the Cognito User Pool configuration using an Implicit Grant setting which enables a user to obtain tokens, I was able to view the Hosted UI.
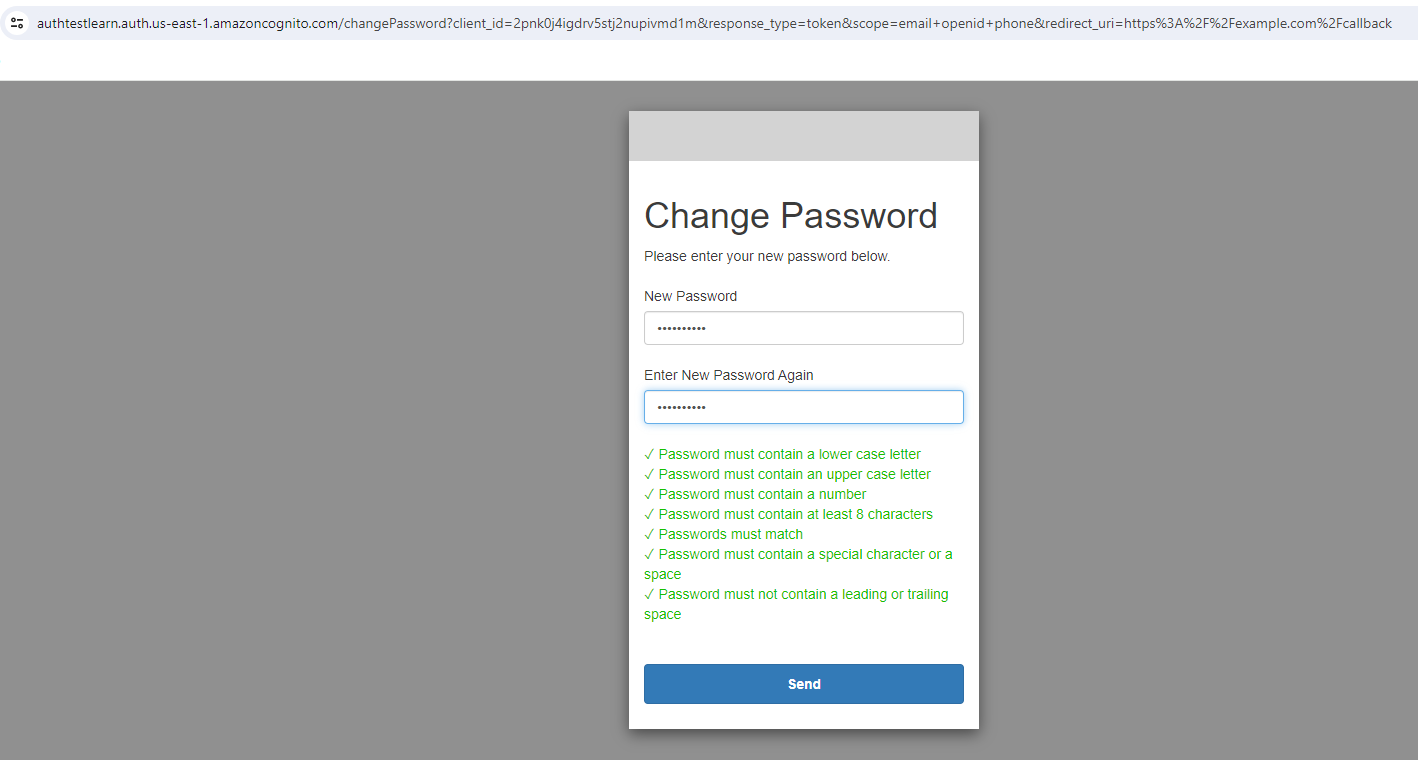
However, at this point, I had no user account to test with. I returned to Cognito and created a user account with a verified email address. I returned to the Hosted UI and logged in. After changing my password, I was issued with an ID and Access authentication token.
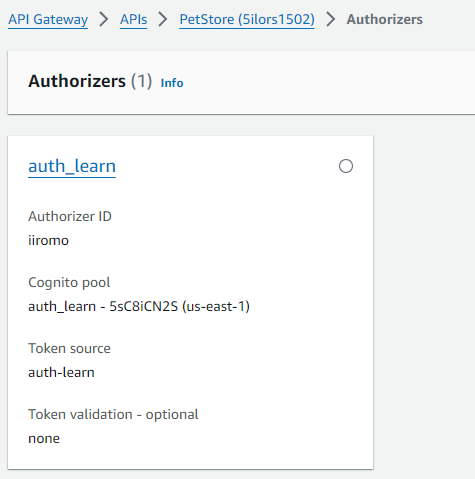
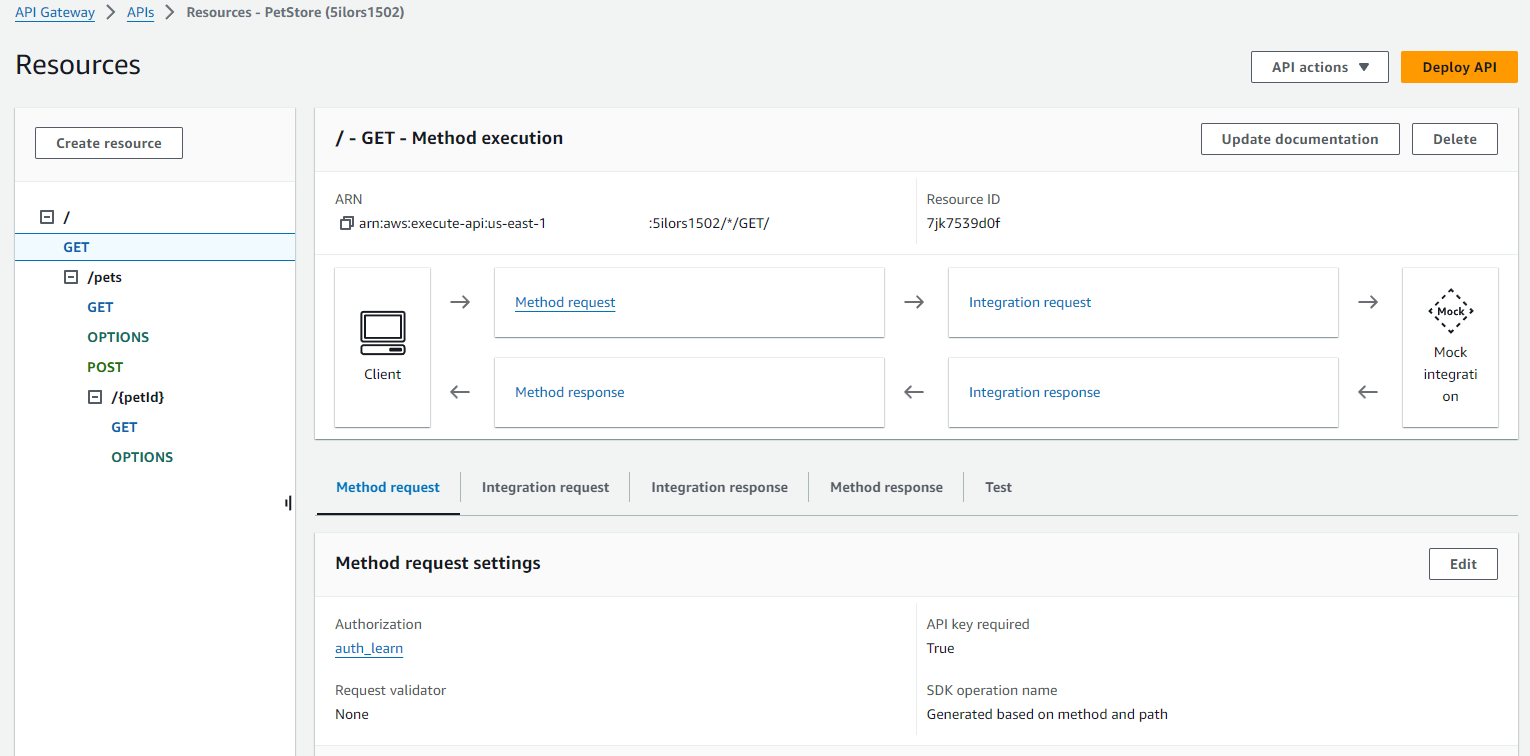
My API was still publically accessible at this stage, so I returned to the API Gateway and set up a Cognito Authoriser.
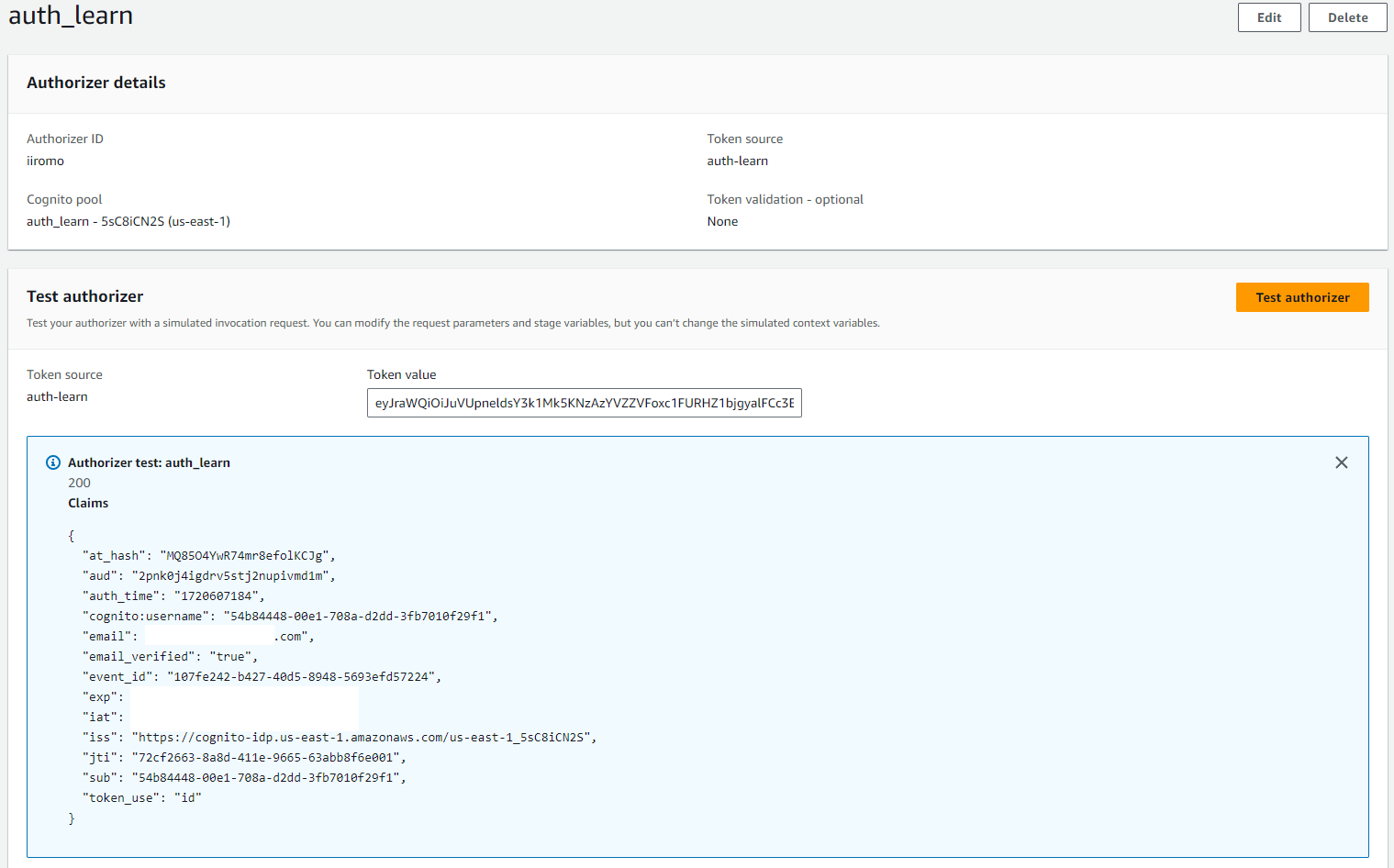
I tested the ID token issued against the Authoriser and confirmed a successful authentication “200 response”.
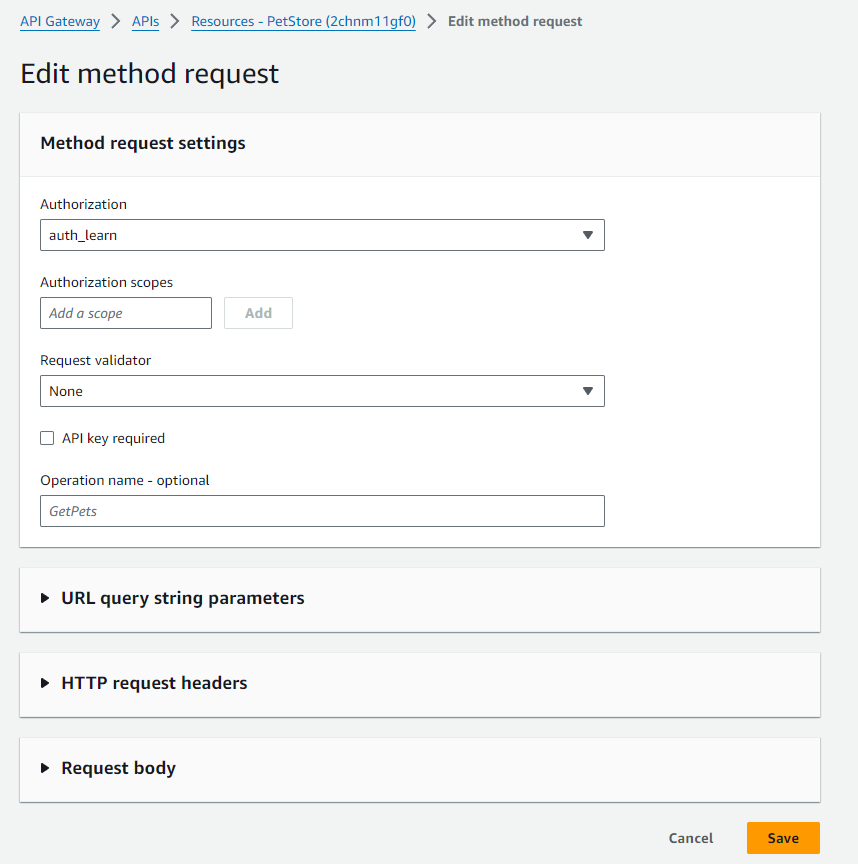
I then linked my Cognito Authoriser to my API method request and deployed the API again.
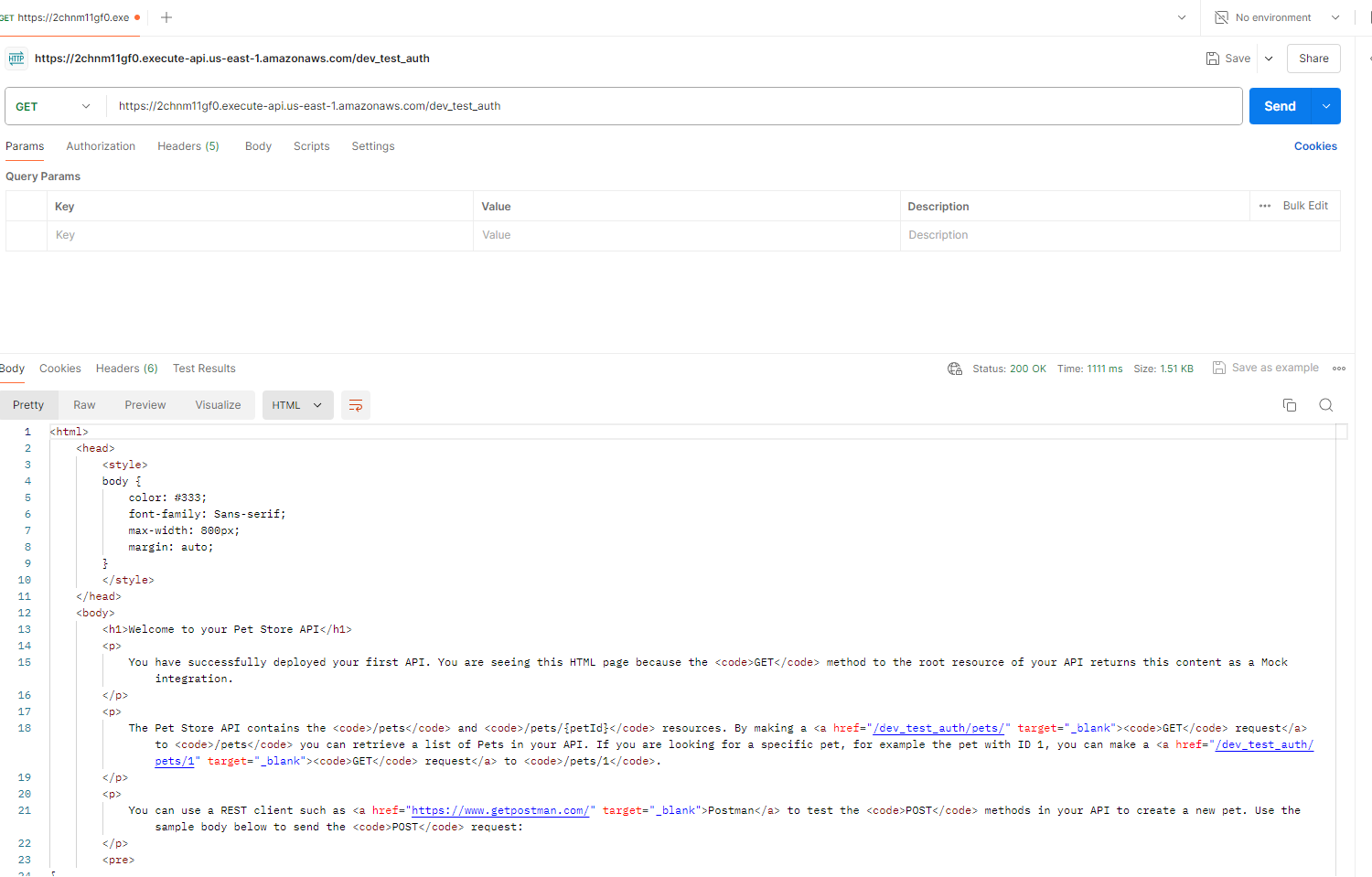
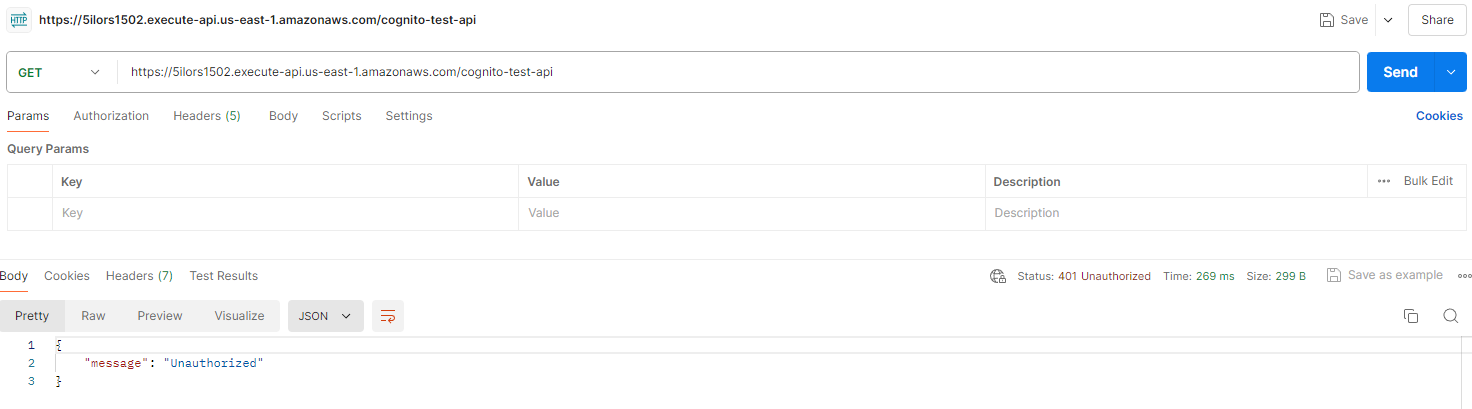
After returning to Postman, my calls to the invoke URL without a token were now failing which is great! My authoriser will block requests without a token in the header.
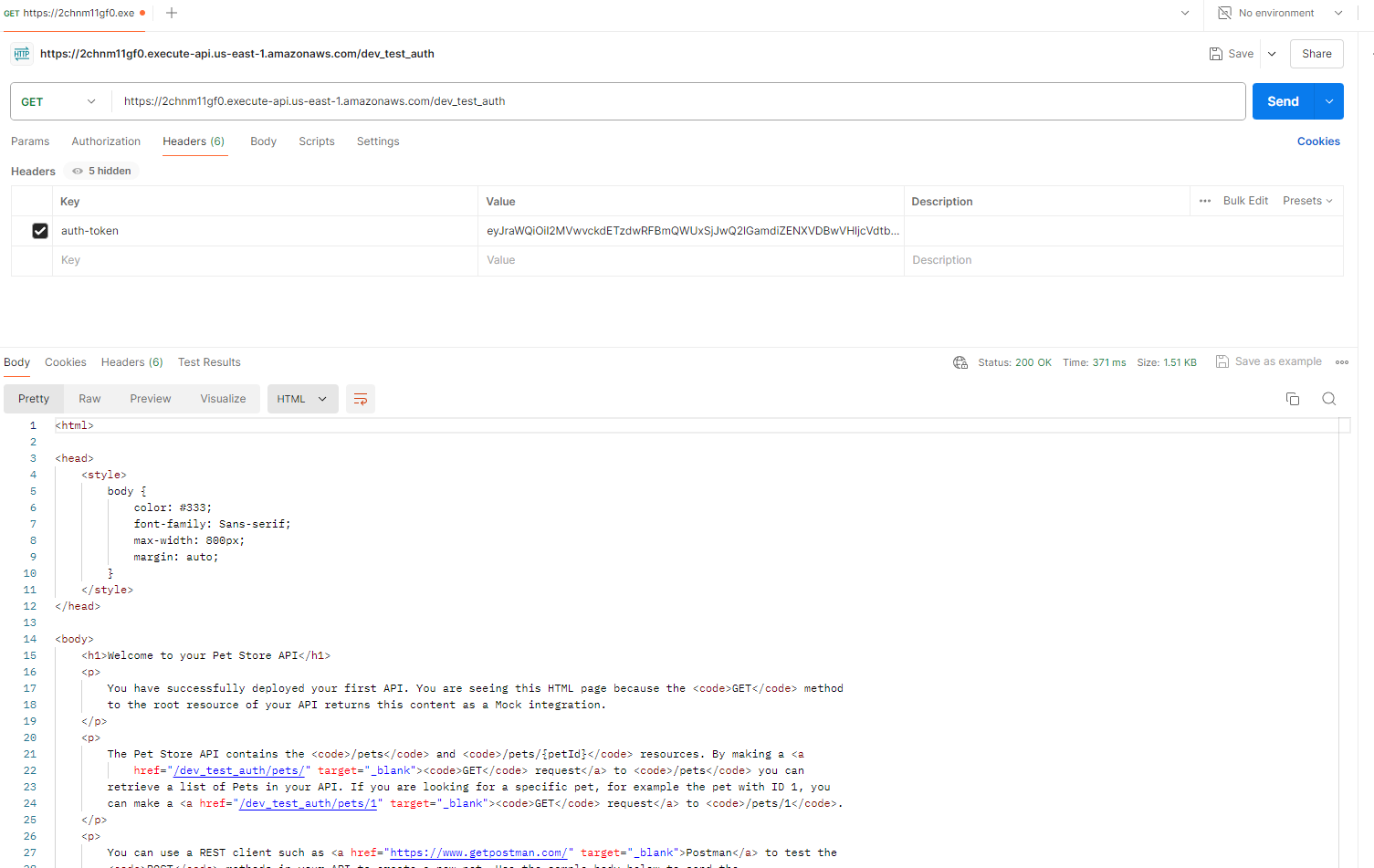
I obtained the authorisation token, added it to the Postman header, and re-tested… success! Calls to my API were now succeeding again with a 200 response and viewable content in the API platform!
This was a great learning experience in API Gateway and how Cognito can be used to create reliable and secure environments!
Some of the highlights…
API configured:
Postman API successful: [no auth token required]
Cognito User Pool:
Cognito HostedUI:
New user sign-in:
Authenticated user:
Access to the website:
Authentication token:
Cognito Authoriser:
ID Token test:
API Gateway method request update: [embedding the Cognito Authoriser]
API Gateway method request Resources:
Postman API failing: [auth token now required]
Postman call succeeding: [auth token header added]
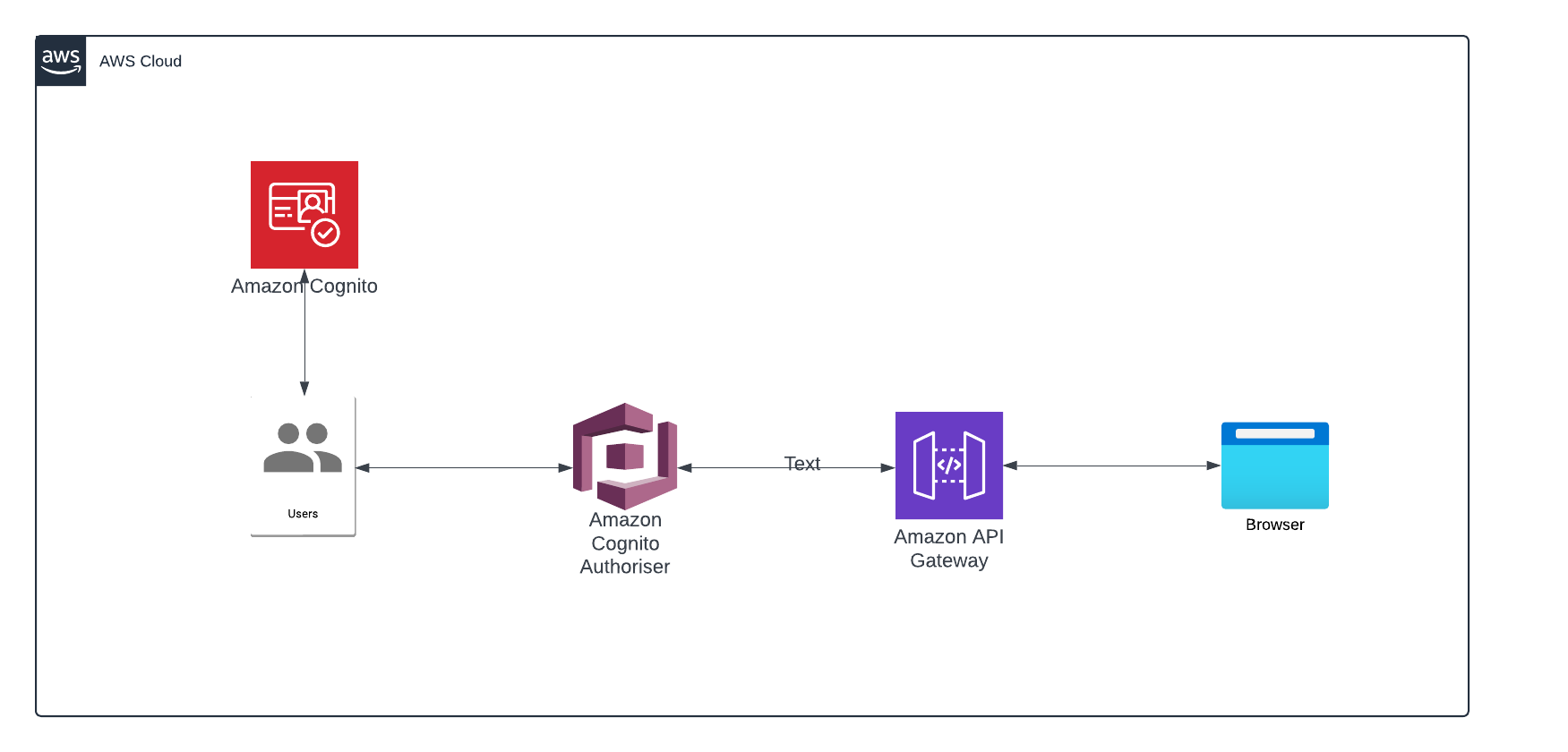
My interpretation of the architecture:
I hope you have enjoyed the article!